If you have ever paused a release because someone mentioned SOC 2 at the last minute, you already know how quickly a security requirement can turn into a full stop.
Many growing engineering teams hit a point where informal security practices no longer satisfy enterprise clients.
At that stage, SOC 2 compliance appears less like a nice-to-have and more like a minimum bar for being taken seriously as a service organization.
The path to a SOC 2 report may feel vague at first, and the terminology can sound heavier than it actually is.
When a team tries to meet SOC 2 requirements without help, the work tends to get scattered across tickets, half-finished security policies, and spreadsheets that grow harder to update.
You may notice tension creeping in because no one is quite sure when the system is ready for an audit or what evidence an auditor may ask for.
This guide walks you through what SOC 2 compliance requires, how engineering teams typically support the effort, and what best practices tend to make a noticeable difference.
You will see how Trio can step in when compliance needs grow faster than internal capacity, especially for fintech companies aiming for practical, sustainable security instead of check-the-box habits.
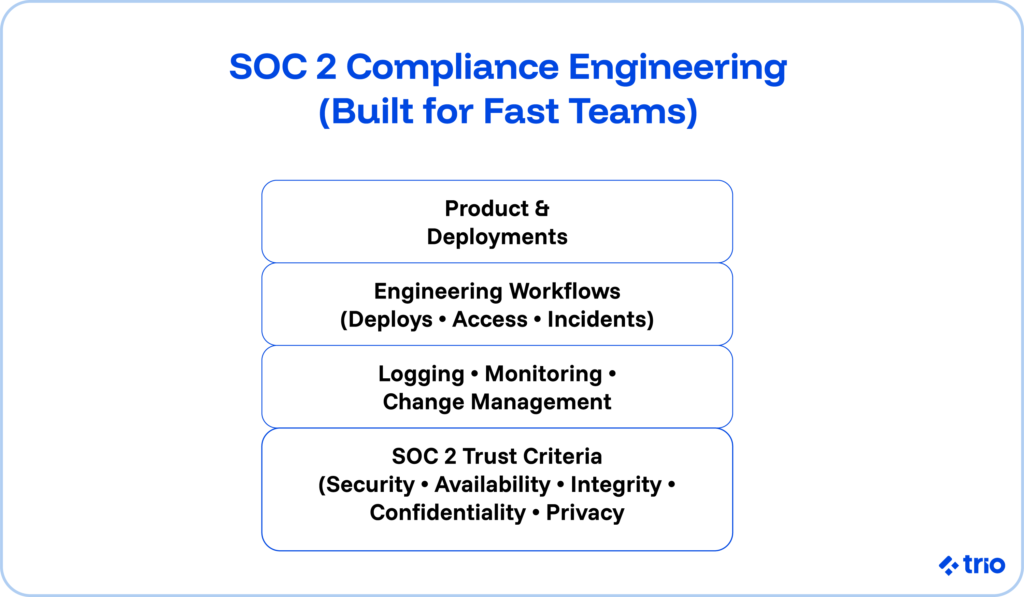
What SOC 2 Compliance Really Means
SOC 2 is often described as a certification, although technically it is an attestation issued by a licensed CPA firm.
A SOC 2 audit evaluates whether you have security controls in place that match the five trust services criteria: security, availability, processing integrity, confidentiality, and privacy.
Most engineering teams focus first on security and availability, then expand as customer demands evolve.
There are two main types of SOC 2 reports. A SOC 2 Type 1 review of your controls occurs at a single point in time. A SOC 2 Type 2 evaluates operating effectiveness across a longer window.
A Type II audit often holds the most weight with enterprise buyers, partly because it shows that your controls work day to day, not just on a good afternoon when screenshots are captured.
For many early-stage SaaS teams, a SOC 2 Type 1 report feels like a milestone, while a Type II report becomes the moment where the company can compete for larger deals.
The Role of Your Engineering Team in SOC 2 Readiness
Your engineering team carries more of the SOC 2 load than most people expect.
Engineers build the controls, instrument the systems, and generate logs that flow into audit evidence.
They also maintain incident response plans, access control policies, change management processes, and onboarding and offboarding processes that determine whether the organization truly follows its security practices.
In day-to-day work, compliance can feel like an interruption. A sudden request from an auditor may pull someone away from a project sprint. A policy update may require new workflows that appear, at first glance, to slow things down.
With the right setup, though, these adjustments blend into normal software development habits.
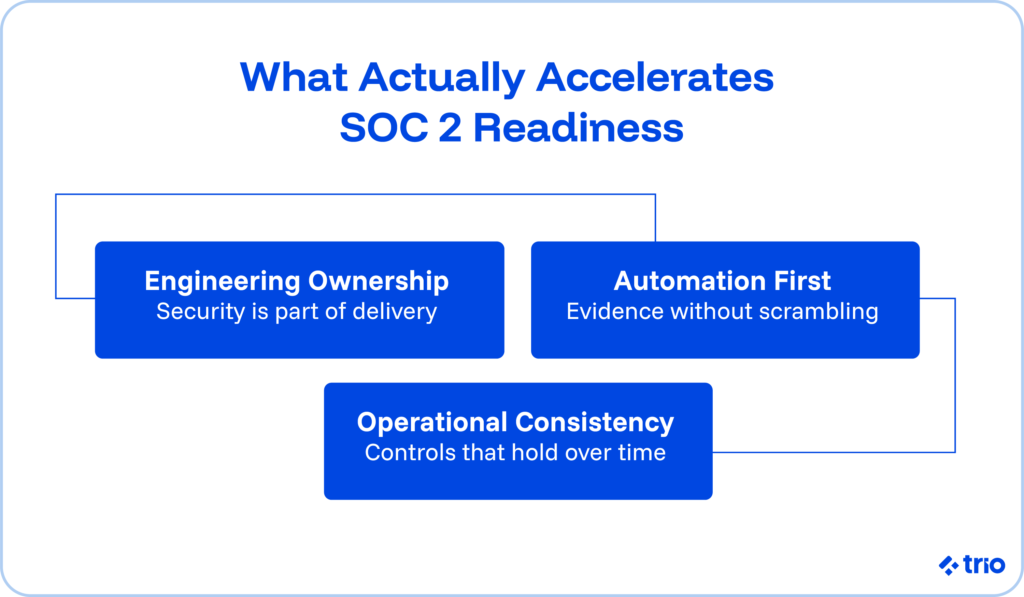
When you treat it as a chance to improve your information security posture through small, controlled steps, the picture becomes more manageable.
Teams that integrate compliance directly into their engineering workflow usually experience fewer surprises during the audit process and gather evidence without late-night scrambling.
Understanding SOC 2 Requirements and Why They Matter
AICPA sets the formal SOC 2 requirements, but engineers often interpret them through the lens of daily operations.
You are expected to maintain access management standards, document change management, create incident response procedures, and enforce security policies without exception.
These are not meant to restrict creativity. They act more like safeguards that keep the organization functioning when something goes wrong.
SOC 2 compliance requires a certain level of operational discipline that younger teams may not have built yet.
For example, automated onboarding ensures the right permissions are applied consistently, while proper vendor management keeps third-party risk under control.
Vulnerability scanning, social engineering awareness training, and evidence collection all contribute to a compliance program that aligns with security frameworks like ISO 27001, even if you are not pursuing that certification.
When auditors evaluate your environment, they look at your controls in place and how effectively you maintain compliance over time.
An SOC 2 audit checks whether your system behaves predictably and whether your commitment to security shows up in the details.
Types of SOC 2 and How They Affect Engineering Work
You may already know the difference between SOC 2 Type 1 and SOC 2 Type 2, but the engineering implications deserve attention.
A Type 1 report helps you show that your control design is sound. A Type 2 report confirms that the controls operate as intended across months, which requires stronger monitoring, consistent processes, and a more mature compliance posture.
Because a Type II audit spans a longer period, engineers usually spend more time refining logging, access control, and change documentation to avoid gaps.
Automating these pieces reduces the risk of missing evidence when the auditor asks for proof. Your team may also need to adopt a compliance platform that centralizes workflows and reduces friction between departments.
This step becomes even more helpful when security and compliance standards need to be shared with customers or internal stakeholders.
How SOC 2 Auditors Evaluate Your System
An auditor from a licensed CPA firm examines your controls, tests your operating effectiveness, and issues a SOC 2 attestation once the audit process ends.
Their findings feed into the SOC 2 reporting process that prospective clients often request before signing a contract.
Although this may sound uncomfortable, a good auditor aims to confirm what you already know.
They review access logs, change tickets, code deployment workflows, vendor tracking, and risk management documentation.
If you approach SOC 2 readiness as an extension of your engineering workflow, preparing for the seamless audit feels much easier.

Best Practices Engineering Teams Lean On
A few habits tend to reduce compliance stress significantly.
- Integrate audit readiness into your build process instead of saving it for later.
- Automate evidence where possible, so you are not chasing screenshots
- Track vulnerabilities and patch timelines with enough clarity to share during a type II audit
- Keep documentation close to the workflow so it stays current
These steps may suggest additional work early on, but they prevent urgent compliance tasks from disrupting product momentum.
The teams that achieve SOC 2 compliance with less pain often start small and build consistently.
Where SOC 2 Services Fit Into the Picture
You can manage SOC2 requirements internally, but many engineering leaders eventually bring in outside SOC2 services or consultants.
The goal is not to outsource thinking but to avoid unnecessary detours.
Experts help translate compliance language into practical engineering tasks.
They also guide the organization through the compliance process, highlight which security controls matter most, and support teams through the long stretches of a Type II audit.
If you are operating in regulated industries or working toward additional standards like the cybersecurity maturity model certification, the guidance becomes even more valuable.
Security and compliance are not static; new threats, new customers, and new integrations constantly shift expectations.
When a Compliance Platform Makes Sense
Once your organization grows, spreadsheets stop working. A compliance platform reduces manual effort, tracks outstanding work, and centralizes audit evidence.
Some companies adopt automation early to support a growing engineering team, but others wait until they feel the strain.
Either way, a platform gives you a single view of your controls, security practices, and overall security posture.
Automation does not replace human judgment. It helps you maintain compliance consistently and meet SOC 2 requirements without relying on memory or scattered notes.
With the right setup, you will catch gaps earlier and avoid long delays before the audit begins.
A Closer Look at Readiness, Evidence, and the Audit Window
Audit readiness means being able to prove what you claim. Evidence collection can be the most time-consuming part of the SOC 2 journey if handled manually. Logs, screenshots, change records, and access reviews all play a part.
When your systems are instrumented well, evidence emerges naturally from daily work instead of being manufactured at the last second.
Engineers often feel nervous about whether an auditor will find small gaps. In practice, auditors want to understand how you operate and whether controls function consistently.
Honest records and clear processes matter more than flawless execution. If you show that you identify and fix issues through thoughtful risk management, your compliance program looks stronger, not weaker.
Why Trio Helps Teams Move Faster Toward SOC 2
Trio has supported engineering teams across fintech companies that needed to meet SOC 2 requirements while continuing to ship.
Some organizations come to Trio after realizing that their internal bandwidth cannot sustain both engineering progress and audit preparation.
Others reach out because they want a practical partner who understands how to translate compliance expectations into engineering workflows without slowing them down.
Our engineers help teams tighten access control, refine deployment processes, introduce change management where gaps exist, and prepare the environment for a SOC 2 Type 1 or SOC 2 Type 2 audit.
When controls must be implemented in complex systems, we combine security knowledge with hands-on software development experience.
Working with Trio may also reduce long-term maintenance effort.
Instead of scrambling to maintain compliance each year, your team ends up with cleaner workflows, stronger monitoring, and fewer surprises during renewals.
Compliance automation, vendor tracking, audit readiness checkpoints, and structured incident response patterns all become part of daily engineering life, not just a pre-audit scramble.
Security and Compliance Continue After the Report
Receiving your SOC 2 report does not mark the end of the journey.
You maintain compliance year-round, which means adapting security controls as new tools, new hires, and new integrations enter the environment. The controls work only when the entire team treats them as part of normal behavior.
As your organization grows, you may implement new security frameworks or revisit older decisions, especially when enterprise clients ask questions about operating effectiveness or specific controls in place.
The habits formed during SOC 2 lay a foundation for stronger data security, healthier risk management discussions, and improved customer trust.
Companies that embrace this continuous mindset usually experience clearer communication between engineering, operations, and leadership.
You notice issues earlier, make decisions more confidently, and treat cybersecurity and compliance as part of good product stewardship rather than an external burden.
Final Thoughts
SOC 2 is not simply a hurdle. It is a commitment to security that signals maturity to customers and partners.
The audit may feel intimidating at first, but once your engineering team has the right structures in place, the process becomes a predictable part of company growth.
Tools, platforms, and outside expertise can help, but your internal habits ultimately shape your compliance posture.
If you find yourself juggling product work with SOC 2 readiness and could use engineering support that understands the practical realities, Trio can help you meet SOC 2 requirements without losing momentum.
Many companies discover that the earlier they bring structure into their compliance program, the easier every future audit becomes.
We have guided organizations of different sizes through this transition with a grounded, engineering-first approach.
If you are preparing for a SOC 2 audit, expanding into new markets that require stronger guarantees, or simply aiming to strengthen your security practices, get in touch.
FAQs
What is SOC 2 compliance?
SOC 2 compliance means your organization follows defined security and trust criteria. Meeting SOC 2 compliance shows customers that you protect data consistently and can prove it during an audit.
How long does it take to get a SOC 2 report?
Getting a SOC 2 report usually takes several weeks for Type 1 and several months for Type 2. The timeline depends on how prepared your controls and documentation are before the audit window begins.
Do engineering teams really need to be involved?
Engineering involvement is essential because engineering teams maintain the systems and controls that SOC 2 requirements depend on. Their work produces the evidence that auditors review.
What’s the difference between SOC 2 Type 1 and Type 2?
The difference between a SOC 2 Type 1 and Type 2 report is that Type 1 checks controls at a single moment, while Type 2 evaluates operating effectiveness over time.
Can small companies achieve SOC 2?
Small companies can absolutely achieve SOC 2 compliance, and many do earlier than expected. The main hurdle is organizing processes so they work reliably even with limited staff.
Do we need a compliance platform?
Needing a compliance platform depends on how complex your environment is and how much manual tracking you want to avoid. Teams with fast growth typically adopt one to reduce missed evidence and duplicated effort.
How much does an SOC 2 audit cost?
The cost of an SOC 2 audit varies based on the audit scope, company size, and auditor selection. Most organizations budget a few thousand to several tens of thousands for a full engagement.
Can outsourced engineers help with SOC 2 readiness?
Outsourced engineering support can help with SOC 2 readiness by building or refining controls, writing documentation, and preparing evidence. Many teams use outside help to keep product timelines intact.
What happens if we fail part of the audit?
Failing part of a SOC 2 audit results in exceptions in your report rather than a total failure. You can remediate the issues and strengthen controls before the next audit cycle.
How often do we need to renew SOC 2?
SOC 2 renewal typically happens annually to show ongoing compliance. The repeat cycle reassures customers that your controls continue to operate effectively.