You probably already feel the pressure around compliance.
It sits in the background of every product decision, every infrastructure choice, and every conversation about scaling securely.
PCI DSS compliance may seem like yet another obstacle piled on top of real product work, but for anyone handling cardholder data, it becomes part of your engineering culture whether you intended it or not.
Let’s walk you through what PCI compliance actually requires, how the 12 requirements translate into day-to-day engineering decisions, and where engineering help makes the biggest difference.
And because teams often underestimate how much time compliance eats up, you’ll see how support from fintech specialists like Trio can offset the load while keeping your roadmap intact.
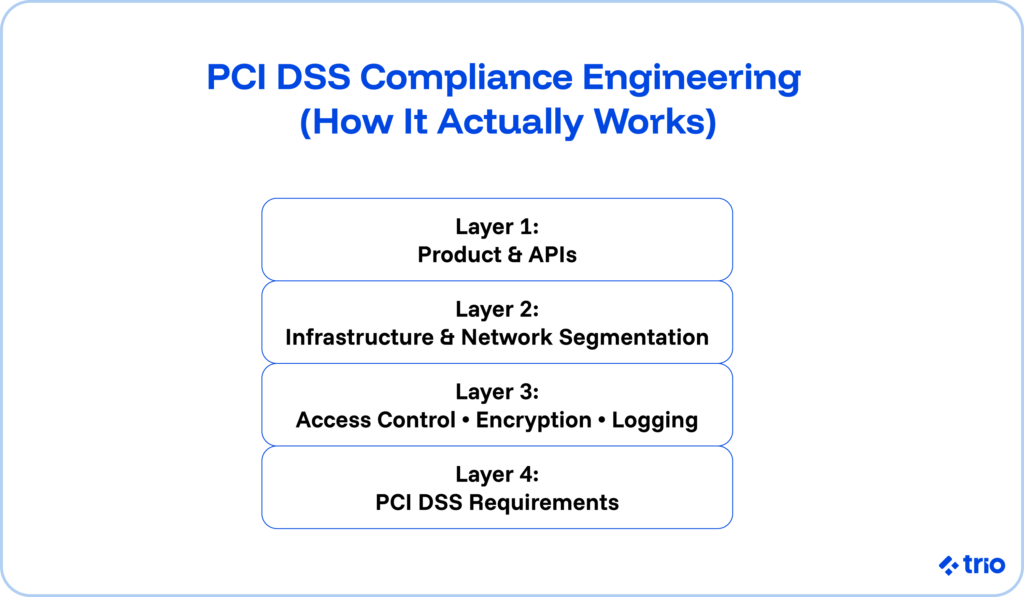
What PCI DSS Compliance Really Means for Your Engineering Team
PCI DSS (the Payment Card Industry Data Security Standard) exists to protect cardholder data during credit card transactions and throughout the systems that store, process, or transmit payment card information.
The PCI Security Standards Council sets the rules, maintains updates such as PCI DSS v4.0, and defines the security requirements service providers and merchants must follow.
Although compliance applies across industries, fintech teams face a unique reality.
You’re moving quickly, building new payment flows, and experimenting with architectures that may increase your PCI scope without warning.
A single new endpoint can drag additional systems, logs, or S3 buckets into the compliance boundary.
Your engineering choices affect whether you remain PCI compliant, need to reduce your PCI scope, or accidentally expand it.
If you’ve ever felt surprised during a report on compliance, you’re not alone.
Compliance isn’t a one-time task. It’s more of an ongoing compliance practice that touches design, infrastructure, code reviews, monitoring, and how your team handles customer data.
That’s why teams often look for PCI compliance engineering help before a deadline rather than after a data breach.
Understanding the PCI DSS Levels and Why They Matter
The PCI compliance level you fall into depends on the number of credit card transactions you handle in a year.
Some companies underestimate their level because they process through a gateway, but card brands require different validation steps based on volume.
A higher level (such as PCI DSS Level 1) usually requires an on-site audit performed by a Qualified Security Assessor, plus more extensive documentation.
Lower levels may allow a Self Assessment Questionnaire.
Either way, you’re responsible for the cardholder data environments you manage. And if you handle card information, even temporarily, you need to be PCI compliant.
When engineering teams start scaling and traffic jumps, the shift between levels of PCI compliance can happen faster than expected. Planning ahead saves time that would otherwise go into rushed remediation.
The 12 PCI DSS Requirements, Explained from an Engineering Perspective
You’ve likely seen the list before, though it may feel abstract until you map it to your infrastructure.
These 12 requirements appear to be straightforward, but in practice, they influence your architecture, your security policies, your monitoring, and the workflow your engineers follow.
A brief look at how they show up in real engineering work:
- Build and maintain secure networks: Firewalls, network segmentation, and access rules often determine your PCI scope. A poorly segmented network tends to be the biggest source of unexpected findings.
- Protect cardholder data: Encrypting card data at rest and in transit seems simple, yet real-world implementations create edge cases around logs, backups, analytic pipelines, and message queues.
- Maintain a vulnerability management program: Patch cycles, automated scanning tools, and container updates all feed into this. Teams sometimes skip routine patching when release cycles speed up, which causes issues during validation.
- Implement strong access control measures: Engineers may not love frequent permission audits, but PCI requirements expect strict role-based access to systems storing payment card data.
- Monitor and test networks: Continuous logging, intrusion detection, and alerting pipelines have a direct impact on your compliance status and your ability to respond to a security issue.
- Maintain an information security policy: This is where engineering teams often underestimate the effort. Policies become living documents and should reflect how your stack changes over time.
The PCI Data Security Standard expects you to apply these requirements across the entire cardholder data environment.
If your architecture is distributed or microservice-heavy, you may have considerably more work than the original checklist suggests.
PCI DSS v4.0 and What’s Different Now
PCI DSS 4.0 introduces a more flexible approach where you can either follow the defined method or justify a customized one.
Some teams like this. Others find it creates uncertainty since you now need to validate compliance for non-standard controls.
This version of the PCI DSS updates logging, authentication, and testing rules, and strengthens requirements for service providers.
If your team is in the middle of rewriting a payments module or migrating infrastructure, timing the switch to 4.0 compliance can be frustrating.
Still, PCI DSS 4.0 pushes engineering teams toward practices that are already considered modern security hygiene.
You may find that adopting it early makes your systems tighter and reduces panic during your next audit.
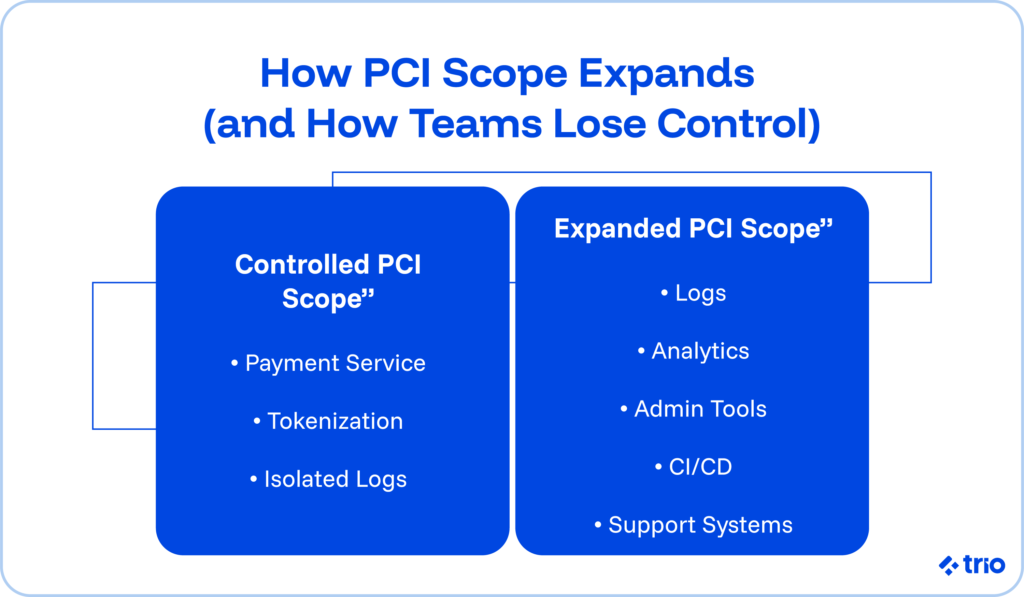
Compliance Requirements That Usually Surprise Teams
Most organizations expect encryption and firewalls. What catches teams off guard tends to be smaller, more operational rules.
A few examples:
- Storing card data in logs without realizing it: A verbose debug mode or a misconfigured logging library can accidentally write sensitive card information into log storage. Engineers often spot this late.
- Shadow systems that store customer data: A simple analytics pipeline or a forgotten test database sometimes contains cardholder data months after deployment.
- Tools that expand PCI scope unintentionally: CI/CD systems, support dashboards, internal admin panels, or even Slack integrations may touch card data without anyone noticing.
Once these show up in your compliance checklist, remediation becomes a cross-team task rather than a quick fix.
Why Engineering Help Makes PCI Compliance Manageable
Many fintech teams reach a point where compliance requirements slow product development.
It isn’t because engineers don’t understand security. It’s because PCI compliance requires time, consistency, and a habit of thinking several steps ahead.
External PCI compliance engineering helps give you an engineering partner who already knows the card industry data security standard.
When your team doesn’t need to pause and learn the basics, compliance tasks move faster.
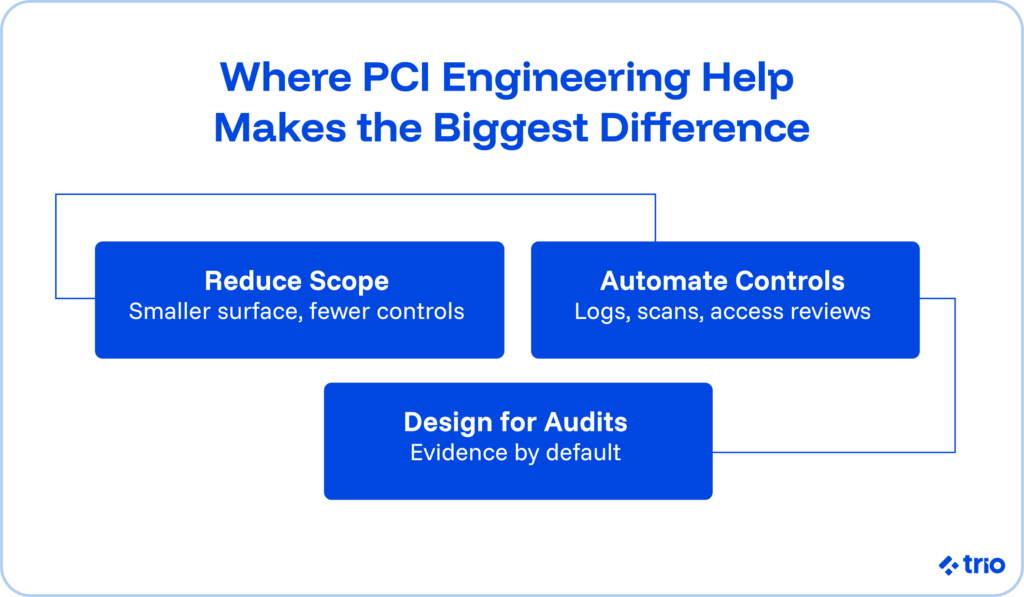
Support that reduces your PCI scope
A specialist can help rearchitect high-risk paths, introduce tokenization, or isolate sensitive data so the audit footprint becomes smaller.
The ability to validate compliance early
Catching issues before a report on PCI compliance or an attestation of compliance saves weeks of scrambling.
Practical guidance on meeting PCI requirements without slowing your roadmap
Compliance shouldn’t dictate your product direction.
This is precisely the type of engineering support that Trio provides.
Our engineers understand cardholder data flows, payment infrastructure, regulatory compliance, and the realities of shipping code under pressure. They integrate quickly into fintech teams and speak the same language your auditors use.
What PCI Compliance Best Practices Look Like in Real Life
The phrase “best practices” sometimes feels too generic, but these patterns show up repeatedly in teams that maintain PCI compliance with fewer headaches:
- Lean, clearly defined PCI scope: You may not need to store payment card data at all. Tokenization or third-party vaults reduces risk substantially.
- Infrastructure designed for segmentation: This helps protect card data and keeps unrelated systems out of audit range.
- CI pipelines that enforce compliance steps automatically: Automated tests for dependency versions, hardcoded secrets, and encryption settings prevent regressions.
You don’t need to overhaul everything at once. Compliance steps added gradually usually hold up better than rushed overhauls.
The Role of the PCI SSC and How It Affects Your Architecture
The PCI Security Standards Council publishes updates, clarifies rules, and helps enforce alignment between card brands, merchants, and service providers.
Even if you never speak directly with the PCI SSC, their standards influence decisions such as how you log events, how you rotate keys, and what minimum authentication settings you enforce.
Ignoring these guidelines creates a long tail of unexpected engineering work. Following them keeps your compliance program predictable and prevents your team from having to retrofit fixes across the entire stack.
Mapping PCI Requirements to Modern Fintech Architectures
You may work with cloud native services, distributed data pipelines, or hybrid systems that pull in third-party providers.
PCI requirements apply across the full chain, including your vendors. That’s why validating service providers becomes such an important part of compliance with PCI DSS.
As architectures become more complex, compliance practices must adapt.
The engineering mindset shifts from “how do we check off these controls” to “how do we design systems that naturally meet compliance standards without forcing workarounds.”
This shift usually happens once a team assigns explicit ownership for PCI DSS compliance, either internally or through external help.
PCI Compliance Starts With Understanding Your Scope
One of the simplest but most often overlooked steps is identifying where payment card data flows, where card information is stored, where it might leak, and which systems fall inside the PCI scope.
Even small misunderstandings can expand your scope dramatically. A single misrouted message queue, for example, may lead to card data landing in unexpected places.
When you work with specialists who understand these patterns, you avoid spending weeks untangling your own data maps.
Learn What PCI Requires Before You Architect
Every engineering project that touches customer data or payment card data should start with clarity around compliance obligations. When teams skip this, they end up retrofitting protection later, which is slow and expensive.
For example, storing credit card data directly rather than via tokenization increases maintenance, monitoring, validation, and risk. Architects who understand PCI standards design with these constraints in mind from the beginning.
This is an area where Trio’s background in security engineering makes a difference. They know how to help teams meet PCI requirements while still delivering at startup speed.
How To Achieve Compliance Without Losing Momentum
Engineering teams tend to fear audits more than the compliance process itself. A better way to think about it is like ongoing hygiene. You build habits that prevent large surprises.
A common approach looks something like this:
You start by validating where card data moves. Then you apply the core PCI DSS requirements gradually, and you automate the parts that feel repetitive, like scans, logs, and access reviews.
When you address compliance through engineering rather than paperwork, you achieve PCI alignment faster and maintain PCI compliance more easily.
Your end goal isn’t perfection. It’s a compliance strategy that strengthens your infrastructure and reduces your long-term risk.
A Guide to PCI Compliance for Teams Growing Quickly
Fast-growing fintech companies move faster than their security processes.
You’re likely to expand into new features that involve card information, and earlier decisions follow you. Technical debt affects compliance as much as functionality.
The number of systems collecting logs grows as you ship more services. Log scrubbing becomes essential.
Your compliance status fluctuates when new tools join your stack, especially analytics services that ingest customer data.
If you recognize these patterns, you’re in the same position as many engineering leaders when trying to maintain PCI as their teams expand.
Beyond Compliance: Building Long-Term Trust
PCI requirements aim to reduce card fraud, protect cardholder data, and prevent a data breach, but the deeper value comes from trust.
Customers assume their payment card information is safe. Investors assume you can manage risk. Partners assume you uphold payment card industry security standards without shortcuts.
Compliance means following the rules. Building trust means treating security as part of your product, not a defensive layer you revisit once a year.
When your engineering team treats compliance as part of the development culture, life gets easier. Deployments become smoother, audits become routine, and onboarding new engineers feels less chaotic because your expectations are already clear.
When You Need to Be PCI Compliant Fast
Sometimes you don’t have the luxury of a long preparation window. A bank partner may request new documentation, or maybe you discovered card data in logs unexpectedly and must remediate quickly.
In situations like these, PCI compliance requires calm, structured engineering help. You need people who already understand the PCI process, how to run a PCI checklist, how to prepare a report on compliance, and how to design controls that auditors accept.
This is where outside engineering support becomes valuable because they slot into your workflow immediately, rather than learning your stack from scratch.
Why Fintech Teams Turn to Trio for PCI Compliance Engineering Help
As a company built exclusively around fintech engineering, Trio understands compliance within regulated environments at a level that most generalist teams can’t match.
Our engineers already know payment card controls, risk controls, and the expectations behind compliance with PCI DSS. They integrate quickly, adapt to existing systems, and help teams meet compliance obligations without slowing product development.
Many teams don’t actually need a massive security overhaul. They need clarity, faster execution, and someone who can anticipate how PCI standards apply to their stack.
Our domain fluency, especially around card industry security standards, helps developers stay focused on product delivery rather than compliance fire drills.
Ready To Strengthen Your PCI Compliance Engineering Efforts?
If you want to validate compliance, reduce your PCI scope, improve security policies, or prepare for PCI DSS 4.0, thoughtful engineering support makes a noticeable difference.
And when that support already understands financial systems, regulatory requirements, and the pressures of rapid product development, you move with more confidence and far less friction.
Get in touch to access industry specialists!
FAQs
What is PCI DSS compliance?
PCI DSS compliance means your organization meets the Payment Card Industry Data Security Standard, and staying compliant requires following its rules for handling and protecting cardholder data.
Why are there 12 PCI DSS requirements?
The reason PCI DSS includes 12 requirements is that the standard groups its security expectations into twelve core areas that together reduce risk and protect cardholder data.
Who needs to be PCI compliant?
Needing to be PCI compliant applies to any business that stores, processes, or transmits payment card data, regardless of size or transaction volume.
What happens if my business isn’t PCI compliant?
Not being PCI compliant exposes you to fines, higher fees, and the far bigger risk of a data breach.
How often do I need to validate compliance?
Validating compliance typically happens annually, although some organizations must submit evidence more frequently depending on their PCI level.
Does PCI DSS apply if I use a third-party payment processor?
Using a third-party processor doesn’t eliminate PCI DSS responsibility because you still handle parts of the cardholder data environment.
What is a Self-Assessment Questionnaire (SAQ)?
A Self-Assessment Questionnaire is a PCI-approved form you complete to confirm your environment meets the requirements that apply to your business model.
Do I need a Qualified Security Assessor (QSA)?
Needing a QSA mostly depends on your transaction volume and PCI level, since larger merchants must undergo a formal on-site assessment.
What is PCI scope?
PCI scope describes every system, process, and data flow that touches cardholder data and determines how much of your environment falls under PCI rules.