The fintech world moves fast, and so do potential threats.
Application programming interfaces (APIs) are the hidden highways of modern financial services, connecting banks, payment providers, wallets, and third-party apps. But those highways can also become target zones if security measures aren’t built in from the start.
As more banking functions shift online and open-banking frameworks become standard, every exposed API endpoint or weak credential may open the door to a serious breach.
At Trio, we believe that treating fintech API security as an afterthought is no longer acceptable for fintech teams who value trust and scalability.
Our fintech developers have helped prevent countless data breaches by understanding the requirements behind modern security practices and building this security into their code from the ground up.
Understanding API Security in Fintech
Let’s unpack what API security really means, and why it matters so much in the context of fintech and open banking.
What Is API Security?
API security refers to the practices, controls, and processes designed to protect the APIs that enable systems to exchange financial data securely.
In the fintech sector, APIs often carry user account information, payment requests, transaction histories, or identity verification data.
Because they sit between systems, every API call can be both a convenience and a vulnerability.
Why API Security Matters in Financial Services
In banking and adjacent fintech applications, the margin for error is thin.
A misconfigured API could undermine user trust, expose sensitive payment data, or violate regulations.
As open banking grows, fintech companies face pressure to deliver fast, seamless experiences while also keeping customer data safe. Integrating security into the design of every API is no longer optional.
Common Security Threats Facing Fintech APIs
Recognising potential attack vectors helps fintech organisations focus their effort where they counts.
Broken Authentication and Authorization
One of the most common pitfalls is weak authentication, for example, stolen API keys, reused credentials across services, or overly permissive roles.
Attackers who compromise credentials can masquerade as legitimate clients and access sensitive customer data.
Standards such as the Financial-grade API (FAPI) build on OAuth 2.0 and OpenID Connect to add stronger protections around authorization flows.
Data Exposure and Injection Flaws
APIs may unintentionally provide too much data, return overly broad responses, or fail to validate or input properly.
That opens the door to injection attacks or data leaks.
Given how many fintech APIs move payment data, account information, or personal data, even a seemingly narrow flaw can escalate into a major incident.
Man-in-the-Middle (MitM) and Bot Exploits
If API traffic isn’t encrypted or isn’t authenticated correctly, it becomes vulnerable to interception.
For example, a bot may flood API endpoints or use credential stuffing to probe services.
MitM attacks are mitigated by correct transport-layer encryption and token-binding techniques.
Insider and Third-Party Vulnerabilities
Many breaches trace back to trusted partners or internal users who were granted excessive access.
In finance, where ecosystems often include banks, fintechs, aggregators, and vendors, the weakest link may be a third party.
Ensuring every integration abides by security controls helps mitigate this risk.
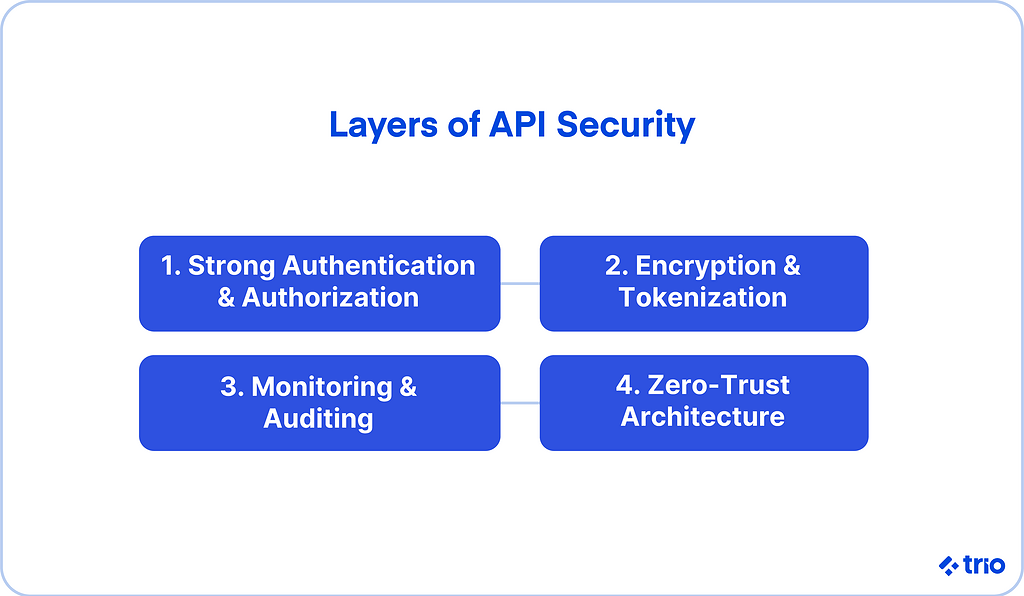
Best Practices for Fintech API Security
Now we move into practical actions: what fintech organisations can do to strengthen their API security posture.
1. Implement Strong Authentication and Authorization
Use OAuth 2.0 and OpenID Connect to manage secure identity and access flows (rather than rolling custom login systems).
For example, short-lived tokens, proof-of-possession methods (such as DPoP), and scoped access reduce risk.
Enforce role-based access control (RBAC) and apply the principle of least privilege: only give systems the minimal rights they need.
2. Encrypt Data at Rest and in Transit
Encryption is foundational. Transport Layer Security version 1.3 (TLS 1.3) offers stronger handshake security, streamlined cipher suites, and mandatory forward secrecy.
For stored data, apply end-to-end encryption and tokenization, especially when handling payment data or personal identifiers.
These measures help ensure that even if a system is compromised through a security breach, data remains protected.
3. Monitor and Detect in Real Time
Security is a continuous process.
Deploy real-time logging and security Information and Event Management (SIEM) tools and anomaly detection (potentially AI-enhanced) to monitor API traffic, authentication attempts, and unusual patterns.
Combine fraud-detection engines and AML integration so security signals and financial risk signals converge.
4. Conduct Regular Security Audits and Testing
Regular vulnerability assessments, penetration tests, and red-team exercises are invaluable for uncovering weaknesses before attackers do.
Relating to APIs, follow frameworks like the OWASP API Security Top 10.
Automate scans during code deployment, moving security testing into the development lifecycle (often referred to as DevSecOps or “shift-left”).
5. Adopt a Zero-Trust Architecture
In a zero-trust model, you treat every system, request, and user as untrusted until proven otherwise.
For APIs, this means segmenting services, using API gateways to enforce policies, verifying each request and device, and isolating access via micro-segmentation.
It changes the mindset from “secure perimeter” to “secure each interaction.”
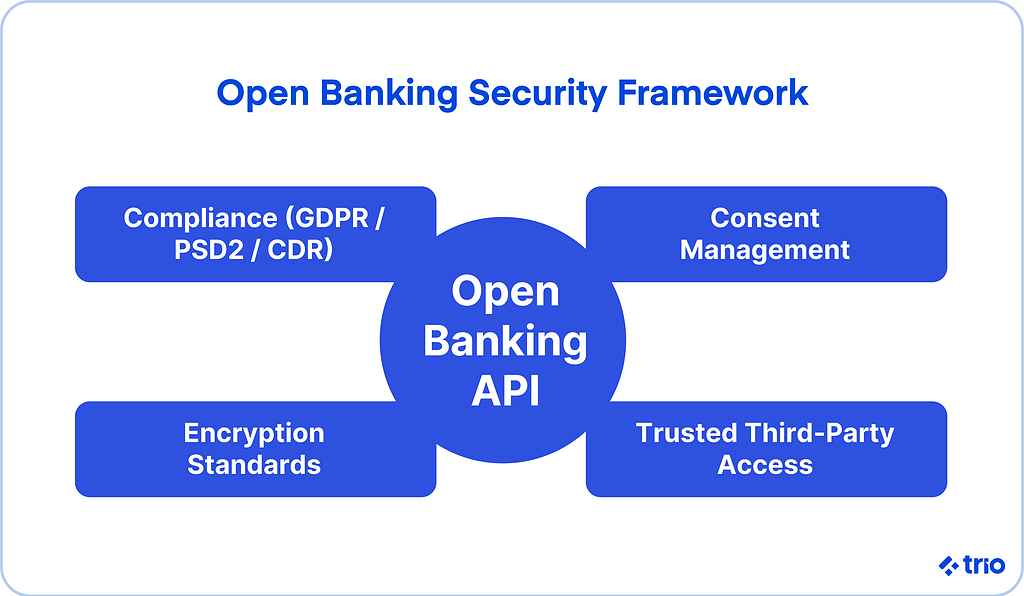
Open Banking and Its Security Implications
Open banking has brought enormous opportunity, but also additional responsibility.
APIs lie at the centre of this transition.
Global Regulatory Context
Regulations such as the European PSD2, Australia’s Consumer Data Right (CDR), and emerging frameworks in other jurisdictions demand secure data sharing, consent workflows, and safe third-party access.
These rules push fintech organisations to treat API security as a compliance priority.
Security Challenges in Open Banking
With open APIs comes a wider attack surface. More endpoints, more integrations, more data flows.
On top of that, fintechs must manage user consent, protect financial data, and ensure third parties are properly vetted.
Mistakes in consent management or mis-scoped access add serious risk.
Security Frameworks for Open Banking
Here are some practical steps: enforce strong customer authentication (SCA), dynamic consent management (allowing users to revoke access), and detailed audit trails.
Aligning with standards such as ISO 27001, PCI-DSS, and GDPR helps ensure consistent data protection.
At Trio, we help fintech organisations build API infrastructures that meet both engineering and regulatory requirements, so security and compliance move in tandem.
Industry Standards and Compliance in Fintech Security
Even when you’ve covered authentication, encryption, and operational rules, the broader context still matters.
Shared Responsibility and Security-by-Design
In finance, your system often links to a network of banks, partners, and vendors.
Security is a collective effort.
Embedding security in API development from the start (rather than as an add-on) helps avoid avoidable risks.
This means secure coding practices, input sanitisation, proper schema validation, and API design that anticipates misuse.
Regulatory Alignment
Beyond open banking, frameworks such as the Digital Operational Resilience Act (DORA) in the EU and financial data-sovereignty rules globally are shaping how fintech companies must protect data and manage risk.
Aligning API security strategy with AML/KYC requirements and cross-border data-flow rules helps fintechs avoid costly missteps.
We work with fintech teams to ensure their APIs are secure, scalable, and compliant across jurisdictions.
Emerging Technologies and Future Trends in API Security
Looking ahead, a few technologies are likely to shift how fintech APIs are protected and managed.
AI and Machine Learning for Threat Intelligence
Modern monitoring systems are increasingly using machine learning to detect anomalies in API traffic: unusual geo patterns, odd request volumes, or newly registered client apps.
These signals help detect subtle attacks earlier and reduce false positives from benign anomalies.
Still, caution is needed: models must be trained carefully to avoid bias or blind spots.
Blockchain, Decentralised Identity and Secure DevOps
Blockchain and decentralised identity (DID) are starting to play a role in how fintechs manage identity and audit trails, giving users more control while reducing centralised risk.
At the same time, DevSecOps practices (like automated security testing during CI/CD) are becoming standard for fintechs wanting to move fast without sacrificing security.
Token binding and proof-of-possession methods (such as DPoP) add further layers of protection.
Quantum-Safe Encryption and Unified Risk Engines
While still emerging, quantum-resistant cryptography is beginning to enter conversations in fintech, especially for systems expected to run for decades.
Also worth watching are risk engines that merge fraud detection, AML, and API security signals into a single view, enabling a more holistic defence.
Case Studies and Lessons Learned
Real-life examples help illustrate how good practices work (and what happens if they aren’t followed).
- Stripe processes millions of transactions a day, uses tokenisation for customer payment data, and rotates encryption keys frequently. These practices help protect payment flows at scale.
- Plaid uses a tokenised data-exchange model, so third-party apps never store raw banking credentials, which reduces exposure when integrating with banks.
On the flip side, API misconfigurations remain a common root cause for breaches when overly permissive roles, exposed endpoints, or old TLS versions are still in use.
A resilient recovery and response strategy (with clear communication, containment, and audit trails) is as important as the initial prevention work.
Preparing for What Comes Next
The fintech industry isn’t slowing down, so we can assume that the number of APIs and integrations will keep rising.
That means developer education, secure coding standards, and active collaboration among fintechs, banks, and regulators will make the difference.
We focus on embedding engineers who understand both the tech and regulatory stacks. By building secure APIs right from day one, fintech teams can scale with confidence rather than patch under fire.
Conclusion
Modern fintech applications rely on open APIs for everything from payments to account access, and those APIs must be treated as critical assets.
By applying strong authentication, encryption, monitoring, and zero-trust design, fintech organisations can protect sensitive data, meet evolving regulations, and preserve user trust.
Security and innovation don’t have to be at odds. With the right approach, fintech companies can deliver seamless services, manage risk, and build their future.
It’s not easy. It may take investment and constant iteration. But it’s worth the effort, and with partners like Trio, you don’t have to go it alone.
If you are interested in hiring expert fintech developers, get in touch!
FAQs
What is API security in fintech?
API security in fintech refers to protecting the digital connections that move banking and payment data between systems from misuse or unauthorized access.
Why is API security important for open banking?
API security is important for open banking because shared access to financial data introduces new risks if authentication or consent controls are weak.
What are common fintech API vulnerabilities?
Common fintech API vulnerabilities include weak authentication, data exposure, insecure endpoints, and poor encryption practices.
How can fintech companies protect sensitive data?
Fintech companies can protect sensitive data by encrypting it in transit and at rest, using OAuth 2.0 and TLS 1.3, and validating every request.
What are the best practices for fintech API security?
Best practices for fintech API security include zero-trust design, continuous monitoring, regular security testing, and strong customer authentication.





